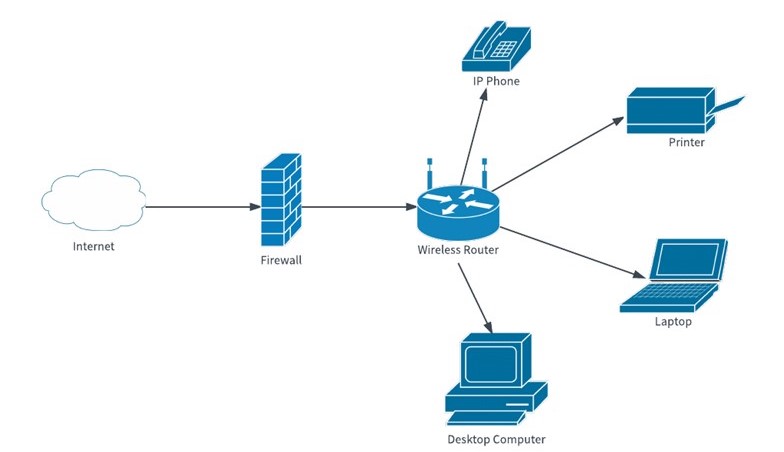
Is your internet service provider mining your data? Is that even legal? Does Your Service Provider Protect Your Data? I don’t know about you, but I wish to keep my private life private. If this sounds like something we have in common, you might be...