Techno Blog
The Most Common Ways Hackers Access Your Network
You are under attack. Right now, cybercrime rings in China, Russia, and the Ukraine are hacking into small businesses like yours to steal credit cards, client information, and swindle money directly out of your bank account. Some are even being funded by their own...
The Hidden Dangers Of “Shadow IT” To Your Business
We all know that using information technology — programs, apps, or internet browsing — carries a certain amount of risk. Nobody wants to have their secure data compromised, but technology brings enough benefits that the risk is worth it. So you vet certain systems,...
The Latest Malware Threat Will Make You Wanna Cry
Wannacry, Wannacrypt, Wannadecrypter, these are just some of the names of the latest string of malware circulating both the news cycles, and the internet. They are all part of a Major Ransomware sting that hit the scene last weekend. In case you don’t know...
4 E-mails You Should NEVER Open
No matter how “bomb-proof” we make your network, you and your employees can still invite a hacker in if you click on a link or open an attachment in an e-mail sent by a cybercriminal. Some spam is obvious (can you say, “Viagra at a discount”?) but others are VERY...
Cybercriminals Confess: The Top 3 Tricks, Sneaky Schemes And Gimmicks They Use To Hack Your Computer Network
We’re masters at getting you to click on fake e-mails. One of the most common ways hackers gain access to computer networks and devices is via phishing e-mails. Gone are the days when you could easily spot a spammer’s e-mail because of its poor English, typos and...
4 Must-Have, Low-Risk Cloud Solutions
Let’s face it, your business has more competition than ever. And they’ll eat you alive if you fall behind in today’s technology “arms race.” Maybe your network needs greater security. Or you haven’t yet taken advantage of new cloud-based apps that help your team get...
Network Abuse: Don’t Push Your ‘Luck’
Look around your office. Isn’t it great to see your team hard at work on their computers? Yet if we take a closer look, let’s see what’s really happening… Joe, your new sales rep, is poring over last weekend’s game stats… Amy in marketing is looking for a new job,...
Lost Employee Smartphone? Do This NOW!
“Hey boss, I lost my smartphone.” How well have you prepared for this moment? It will happen sooner or later. If your company has a plan in place, no big deal. If not, you may suddenly get that sinking feeling in your gut … And well you might. You now have three big...
Don’t Rely on Cheap Online Backups for Your Data!
Last Night I Was Startled Out Of Bed In A Cold Sweat, Heart Racing, With Fear Racing Through My Mind…And YOU Were The Reason For My Panic! Was I having a nightmare? Was I just watching too many reruns of The Twilight Zone? Had I eaten a big meal before bed? No – it...
5 Tools To Keep Your Kids Safe Online
School is in full swing, your kids are digging for the data they’ll need to fill all those reports, papers and projects that fuel their passing grades… And Mr. Google can be their greatest friend when it comes to finding tons of tidbits to keep teacher happy. But with...
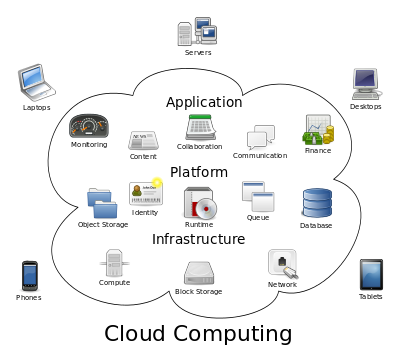
Cloud Computing: Good, Bad & Ugly
When a network of IT gadgets like routers, DVR machines and closed-circuit TVs can take down hardened, well-provisioned Internet giants like Twitter, Spotify and Amazon – as happened last October – you’ve got to think twice before moving your data to the cloud. Yes, a...
Your #1 MUST-DO Resolution For 2017
With every New Year comes the chance to reset priorities. Unfortunately, when the topic of implementing a data recovery plan comes up, the comment we most often hear is “I know I should, but I haven’t gotten around to it yet…” So…what if the pilot on the next flight...
Why Cyberthugs LOVE Your Business
It was a typical morning at the offices of a small Midwestern online retailer. This company, whose name we cannot mention due to a non-disclosure agreement with our source (Gary Miller, GEM Strategy Management) owned a very successful online catalog offering a wide...
5 Common Workarounds For Remembering Passwords, And Why You Should Stop Doing Them Immediately
With everything we do online, it’s impossible to remember all the passwords you need for a web site. So what do most people do? They use one of the following five “workarounds” that make them an easy target for cybercriminals and hackers. Here’s what they are: Using...
The #1 Cure For A Sluggish PC
If you’re often – or even constantly – frustrated with slow loading times, screen freezes or crashing programs, your network may be in desperate need of an upgrade…or a tune-up. Here’s how to make your network run like new again… Most computers and networks bog down...
Winter 2017: Disaster For Your Data?
With winter just around the corner, everyone around you may be getting “all wrapped up” in the upcoming holiday season… But you’ve got a business to run, customers to keep happy and mission-critical data to keep safe, even if a major blizzard, lightning strike,...
Spooked About Your Network’s Security?
You should be, unless somebody’s keeping a vigilant eye on it for you… Not too long ago, in a place not so far away...when ancient hordes attacked your city, a single breach in the wall could mean certain death – or at least the end of life as you know it. Yet times...
The One Attack No Tech Can Stop
You can defend your data with all the latest and best technology. But if just one team member gets tricked into giving away the keys to the castle, it’s game over. Hackers know this. And that's why so many use social engineering to break in. And it’s not just the big...
Lost Employee Smartphone? Do This NOW!
“Hey boss, I lost my smartphone.” How well have you prepared for this moment? It will happen sooner or later. If your company has a plan in place, no big deal. If not, you may suddenly get that sinking feeling in your gut … And well you might. You now have three big...
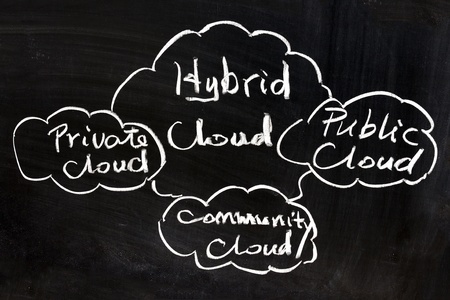
Navigating The Cloud: Gold Mine…Or Minefield?
Is the cloud a good fit for your company or not? On the one hand, taking full advantage of today’s cloud capabilities could be key to becoming a top player in your market. On the other, without proper oversight, just one cyber-break-in could bankrupt your...