COMPREHENSIVE SUPPORT
The Top 10 Ways Hackers Get Around Your Firewall And Anti-Virus To Rob You Blind
Recent Blog Posts
What is Remote Access Software?
Have you ever arrived at the office for the day, anxious about that big presentation you created and practiced last night, only to discover that you can’t find the flash drive containing the file ANYWHERE? With Remote Access Software, you can avoid the stress and...
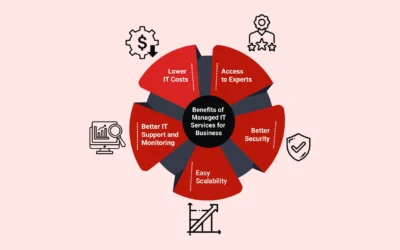
Top 13 Benefits of Managed IT Services for Your Business
The benefits of managed IT services are crucial in today's technology-driven world. So, businesses need to keep up with ever-evolving IT demands while ensuring that their operations run smoothly and securely. However, managing IT systems in-house can be a daunting and...
What is Granular Recovery Technology? A Comprehensive Guide
In today’s data-driven world, information is the lifeblood of organizations. From small businesses to large enterprises, data is the foundation of operations, decision-making, and strategy. With the increasing reliance on digital systems, the need to protect and...