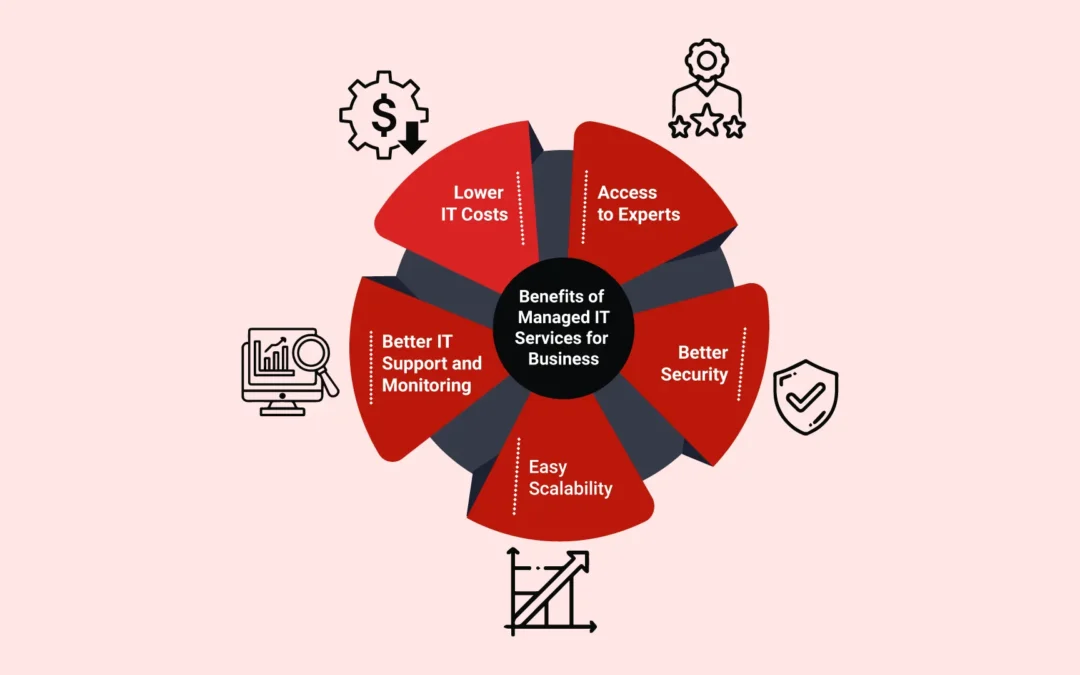
Have you ever arrived at the office for the day, anxious about that big presentation you created and practiced last night, only to discover that you can’t find the flash drive containing the file ANYWHERE? With Remote Access Software, you can avoid the stress and...