Let’s be real for a second: when we think of cyber threats, we usually picture some mysterious hacker in a dark room, tapping away at a keyboard under the glow of a flickering monitor. It’s almost cinematic. But here’s the twist: often, the real threat is much closer to home. Like, sharing your office microwave close.
This is why understanding what an insider threat cyber awareness is matters more than ever in 2025.
We’re living in a time where data breaches can start from a simple, overlooked mistake, or from someone who knows exactly where to hit you hardest. Sometimes it’s malice. Sometimes it’s just plain carelessness. Either way, it hurts.
In this guide, we’ll break it all down: what insider threat cyber awareness actually means, the many faces these threats wear, and why cyber awareness is evolving into a non-negotiable business survival tool. Plus, a few side notes on why trust is complicated and how even good people can sometimes make terrible mistakes.
Spoiler: it’s less about being paranoid and more about being smart. Cautiously smart.
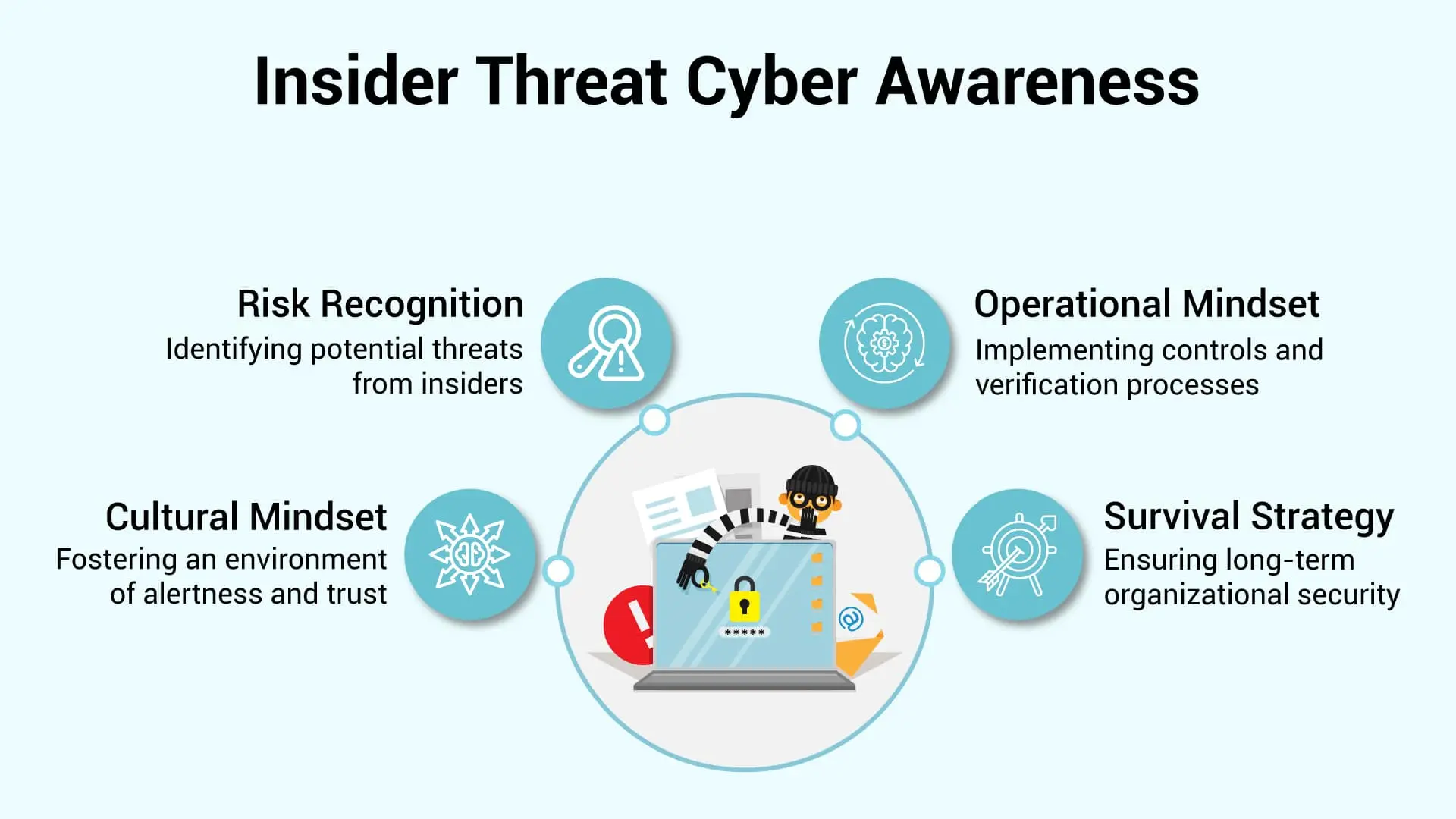
What is Insider Threat Cyber Awareness?
First things first: let’s really unpack the concept.
Insider threat cybersecurity refers to the risks posed by individuals within your organization, employees, contractors, vendors, or even former employees who still have access. It’s an uncomfortable truth, but the ones who know your systems best are often the ones best equipped to break them.

Insider threat cyber awareness, then, is the cultural and operational mindset of recognizing these risks, staying alert, and creating an environment where threats are spotted early, sometimes before the insider even realizes they’re crossing a line.
Awareness isn’t about distrusting everyone. It’s about understanding that trust should always be paired with verification. Not necessarily because you expect betrayal, but because humans are, well, messy. Emotions, distractions, external pressures… all of it plays a role.
If we’re being honest, most companies are a little too optimistic about this. They assume that a friendly office culture will shield them. It helps — sure — but it’s not enough. Having a good vibe and still having strong controls aren’t mutually exclusive. If anything, they should go hand in hand.
And that’s why in 2025, what is an insider threat cyber awareness isn’t just a buzzword or a box-tick. It’s an operating principle. A survival strategy, if you will.
Types of Insider Threats
Now that we know the “what,” let’s talk about the “who” and “how.”
There are several types of insider threats in cyber security, each with its own personality, motivations, and red flags. Some are easy to spot. Others are more slippery.
Here’s the rough breakdown:
Malicious Insiders
These are the ones with clear intent to cause harm. It might be revenge for a perceived slight, financial gain, ideological reasons, or even corporate espionage. They’re deliberate and, unfortunately, often strategic.
Think: a tech engineer downloading proprietary code before jumping ship to a competitor.
Negligent Insiders
Not every threat wears a villain’s cape. Sometimes, it’s just someone who’s rushed, distracted, or unaware. They send sensitive files to the wrong recipient. They forget to log out. They reuse a weak password across personal and work accounts.
No evil intent, but the consequences are real.
Compromised Insiders
Here, the insider is the vehicle, not the driver. Attackers might phish an employee’s credentials and use their account as a gateway. The insider might have no idea anything’s wrong, until it’s very, very wrong.
These cases often go undetected the longest.
Third-Party Threats
Vendors and contractors often need access to internal systems. But their cybersecurity practices? Sometimes… questionable.
If your vendor gets hacked, guess what? You’re in trouble too.

There’s something almost poetic (and frustrating) about how diverse types of insider threats in cyber security can be. It’s rarely neat. Rarely obvious. Which is why insider threat cyber awareness needs to cover a lot of ground.
Because real threats rarely announce themselves.
Real-World Examples of Insider Threats
Stories make things real. Cold facts? They fade. But vivid examples? Those stick with you.
So let’s walk through some cyber insider threat examples that show just how messy, and sometimes tragic, insider threats can get.
- Edward Snowden (NSA): Still debated today, Snowden’s leak of classified NSA data exposed government surveillance practices. Depending on who you ask, he’s either a whistleblower hero or a national security risk.
What’s not up for debate? He was an insider who radically changed global discussions around privacy. - Anthem Healthcare Breach: A compromised employee account led to the breach of almost 80 million health records. No disgruntled rogue actor here, just stolen credentials and a devastating failure to spot the breach early.
- The Coca-Cola Contractor Leak: A former Coca-Cola employee kept sensitive company data on a personal external drive — and then lost it. The breach involved employee records, financial data, and strategic plans.
One forgotten drive. Massive headache. - Tesla’s Insider Sabotage: Tesla reported that a disillusioned employee made changes to manufacturing software and exported sensitive data to outsiders.
Classic case of a malicious insider lashing out internally before leaving.
Notice something? Insider threat types don’t follow a simple pattern. You can’t always profile or predict. That’s the unnerving part.
And why awareness must always, always be evolving.
Signs and Indicators of Insider Threats
You might be wondering, “Is there a checklist to spot insiders before they cause damage?”
Well… yes and no.
The truth is, insider threat indicators are rarely bold, flashing warning signs. They’re more like little puzzle pieces scattered around. Alone, one or two might seem harmless. But when several indicators start popping up together? That’s when you need to sit up and pay attention.
Here are some typical insider threat indicators to keep an eye on:
Frequent use of Unauthorized Devices
Plugging in personal USB drives, using unapproved apps, or connecting unknown devices to the network. (It’s easier than you think for malware to hitch a ride.)
Accessing Systems During Odd Hours
Late-night logins or early-morning access, especially when there’s no clear business need, can sometimes suggest something’s up.
Violation of company policies
Repeatedly ignoring security rules or finding “workarounds” may not seem like a huge deal at first, but casual rule-breaking can hint at bigger, deeper boundary issues.

Behavioral Changes
It’s subtle sometimes, sudden irritability, withdrawal from coworkers, secretive behavior, or even an unexpected enthusiasm for accessing sensitive projects. Changes in mood or behavior, especially after a negative event like a demotion, shouldn’t be brushed off.
Unnecessary Data Hoarding
Downloading way more files than their role demands, copying massive databases, or exporting client lists “just in case” they need them later. (Spoiler: they usually don’t.)
But here’s where it gets tricky, and where many companies go wrong:
You don’t want to create a culture of constant suspicion, where every yawn, frown, or late-night email triggers a full-blown investigation. That’s exhausting. It’s also terrible for morale.
What you want instead is pattern recognition. Systems can help flag the technical stuff, odd logins, massive file transfers, policy violations. But human observation is still crucial too. Managers and coworkers often spot the emotional and behavioral shifts that machines miss.
In other words: yes, be watchful. Notice the signs. But also, don’t lose your mind over every small anomaly. Context matters.
Because at the end of the day, building a resilient, aware workforce isn’t about assuming the worst. It’s about being smart enough — and prepared enough — to act when real red flags start to fly.
The Role of Cyber Awareness in Mitigating Insider Threats
Let’s talk solutions.
Cyber awareness is often dismissed as boring, another compliance video, another forgotten checklist. But it’s actually the foundation of insider threat mitigation.
Good cyber awareness programs:
- Educate employees on phishing, password security, and social engineering tactics.
- Explain why certain security policies exist, not just what they are.
- Normalize reporting suspicious behavior without fear of retaliation.
- Embed security practices into daily operations, not just emergency responses.
Real cyber awareness is about creating a security-first culture without creating a police-state atmosphere. And it takes effort. A lot of it.
And no, a single annual training isn’t enough. It’s like brushing your teeth once a year and wondering why you keep getting cavities.
Cyber Awareness Challenge 2025
Cue the Cyber Awareness Challenge 2025, the latest, and arguably best, version of government-mandated cyber training.
This year’s focus? Drilling down into what is an insider threat cyber awareness 2025, with a particular emphasis on real-world scenarios, interactive decision-making, and human psychology.

It’s not just memorizing terms and ticking boxes. Participants have to navigate nuanced situations — deciding, for example, whether to confront a colleague about suspicious behavior or escalate it to security.
The goal of the Cyber Awareness Challenge 2025 is pretty simple:
- Teach people to think like defenders.
- Train instincts to spot trouble.
- Normalize cybersecurity as an everyday responsibility.
Honestly? It’s a big improvement from the old-school modules. (If you’ve ever sat through a 200-slide lecture on password hygiene, you know the pain.)
And as threats evolve, it’s refreshing to see cyber awareness evolve too.
How to Prevent and Respond to Insider Threats
Let’s get tactical for a moment. Because when it comes to insider threats, good intentions aren’t enough. You need a solid plan.
First up: prevention. It’s easier (and far less expensive) to stop a problem before it explodes.
Least Privilege Access: Only give people the exact access they need to do their jobs. Nothing more. It might feel stingy, but it’s smart security.
Segmentation: Don’t keep all your sensitive data sitting together like a jackpot. Divide it up, protect it separately, and limit who can touch what.
Multi-Factor Authentication (MFA): Passwords alone are no longer sufficient to protect sensitive information. Implementing Multi-Factor Authentication, such as adding a code sent to a phone, creates an extra layer of protection that makes it much harder for stolen credentials to wreak havoc.
Regular Security Drills: If fire drills are second nature, why shouldn’t cyber drills be too? Practice makes panic less likely.
Behavior Analytics Tools: Watch for odd patterns, not individual people. It’s not about spying; it’s about spotting weird, early signs.
Now, what if despite all this, a threat actually surfaces?
Investigate Quietly: Jumping to conclusions publicly can cause chaos, and tip off the culprit. Be methodical.
Isolate the Risk: Quickly limit access, lock down accounts, and contain the problem.
Gather Evidence Carefully: If this escalates legally, how you document things will seriously matter.
Debrief Transparently: Once it’s handled, communicate openly about what happened and how you’ll improve.
Honestly, it’s exhausting sometimes. But not nearly as exhausting as cleaning up a data breach or explaining it to angry customers.
An ounce of prevention really is worth a pound of cure, and in cybersecurity, maybe even more than that.
The Future of Insider Threat Protection
Where are we headed next?
The future of insider threat protection will likely be a mix of:
- Artificial Intelligence (AI): Smart systems predicting risky behavior based on subtle cues humans might miss.

- Zero Trust Models: Trust no one, verify everyone, constantly revalidate.
- Psychological Risk Scoring: (Controversial, but emerging) Using behavioral data to estimate someone’s likelihood of going rogue.
- Gamified Training: Making cyber awareness fun, or at least less soul-crushingly dull.
Yet, even with all the tech advances, one thing won’t change:
Human behavior is unpredictable.
You can build walls, install alarms, and deploy AI. But people will still be people, creative, emotional, brilliant, and sometimes reckless.
The real future? Balancing technology with emotional intelligence.
A machine can spot a login anomaly. Only a human can notice when John from accounting seems unusually bitter after being passed over for a promotion.
Both are critical.
Conclusion
So circling back, what is an insider threat cyber awareness in 2025?
It’s understanding that threats don’t always wear ski masks. Sometimes, they wear name badges and smile at you in the break room.
It’s realizing that prevention isn’t about distrust, it’s about realistic, practical caution.
It’s embedding cybersecurity into your daily life, just like buckling your seatbelt, locking your doors, or double-checking your bank app.
Because in 2025, the best defense isn’t just stronger firewalls or smarter AI. It’s people.
Informed, cautious, engaged people.
And if you’re reading this, you’re already ahead of the curve.