Table of Contents
In today’s connected world, almost everything we do — from work and communication to entertainment and shopping — depends on digital devices and online accounts. That makes one question more important than ever: how can you prevent viruses and malicious code from compromising your digital security?
This isn’t just a tech problem or something only IT teams deal with. It affects everyone. Whether you’re checking emails at home or managing sensitive customer data at work, online threats are always lurking — smart, fast, and often just one careless click away.
We’ve all seen the stories: data breaches, stolen photos, drained bank accounts. The damage can be serious and stressful, both personally and professionally.
That’s why understanding these risks — and knowing how to defend against them — matters. In this guide, you’ll learn practical ways to protect yourself and your business, from simple digital habits to advanced security solutions. Think of it as your step-by-step plan for safer, smarter online security in an always-connected world.
What are Viruses and Malicious Code?

Below is a detailed explanation of the difference between viruses and malicious code. I hope you can understand it better.
What are Virus
A computer virus is a form of malicious code, a digital intruder designed to replicate itself and quietly spread from one device to another. Most people don’t even realize it’s there until damage has already been done. A virus can corrupt important files, leak sensitive data, or completely disable a system.
What are Malicious Code
Malicious code refers to a broader group of threats that includes worms, trojans, ransomware, and spyware. Each behaves a little differently. Worms, for example, spread independently across networks, while trojans disguise themselves as harmless programs to trick users. Ransomware encrypts your data and demands money for the key. And spyware? That one sits quietly in the background, tracking your activity without your consent.
The more you understand these digital threats, the better you can prepare.
Common Types of Malicious Code Attacks
When it comes to cyber threats, there’s no one-size-fits-all villain. Malicious code attacks come in many forms, each with its own behavior, goals, and level of destruction. Understanding these differences is crucial if you want to stand a chance at staying protected.
1st Type: Virus Attacks
Let’s start with the classic virus computer attack. This type of malicious software latches onto legitimate files or programs, almost like a digital hitchhiker. Once activated, it replicates and spreads, often damaging or corrupting files in the process. It’s sneaky, and in many cases, users don’t realize something’s wrong until it’s too late.
2nd Type: Worms
Unlike viruses, worms don’t need a host file to spread. They exploit weaknesses in networks, moving from one device to another, often at lightning speed. One unpatched vulnerability in your system can open the floodgates to a full-blown infection.
3rd Type: Trojans
Trojans take a different approach: they rely on deception. Masquerading as harmless or even helpful software, trojans trick users into opening the door. Once in, they can steal data, install additional malware, or give attackers remote control of your system.
4th Type: Ransomware
Ransomware might be the most terrifying of the bunch. It locks your files, encrypts them, and then demands a ransom to unlock them. Paying doesn’t always guarantee recovery, but many feel they have no other choice.
5th Type: Spyware
Spyware, quiet, persistent, and invasive. It monitors your activity, often collecting passwords, browsing habits, or personal information without your knowledge.
Each malicious code attack targets a different vulnerability. That’s why protecting yourself takes more than just one tool or one habit, it requires a layered, adaptable approach. Because unfortunately, these threats aren’t going away any time soon.
Build a Strong First Line of Defense Against Viruses and Malicious Code
The truth is, once a malicious code makes its way into your system, it’s already an uphill battle. That’s why the smartest move is to stop it before it ever gets in. Building a solid first line of defense isn’t just about having one tool, it’s about putting a few key safeguards in place, each covering the gaps the others might miss.
1st Defense- Start With the Basics: Install Reputable Antivirus Software
It sounds obvious, but not all antivirus programs are created equal. Platforms like Total Defense offer layered protection, scanning in real time, blocking suspicious downloads, and even identifying threats before they become a problem. Whether you’re grabbing it off Google Play, browsing on totaldefense.com, or picking it up through a retailer like P.C. Richard, having it installed is step one.
2nd Defense- Keep Your Software Up-to-date
It’s a step many overlook, but it matters. Every update, whether for your OS, browser, or even apps like Dropbox, often includes security patches for newly discovered vulnerabilities. Skip updates, and you’re leaving the door wide open.
3rd Defense- Use Firewalls as Your Digital Gatekeepers
Firewalls are another essential. Think of them as digital gatekeepers, monitoring the traffic that flows in and out of your system, blocking anything that seems suspicious.
4th Defense- Don’t Underestimate Email Filters
Many attacks begin with a simple phishing email. Good spam filters can stop those threats from ever hitting your inbox.
5th Defense- Create a Layered Security Strategy
Together, these steps form what you might call total defense virus protection, a strategy where every layer strengthens the next. It’s not about being paranoid; it’s about being prepared. Because in the world of cybersecurity, your best bet is to make sure danger never gets a chance to knock.
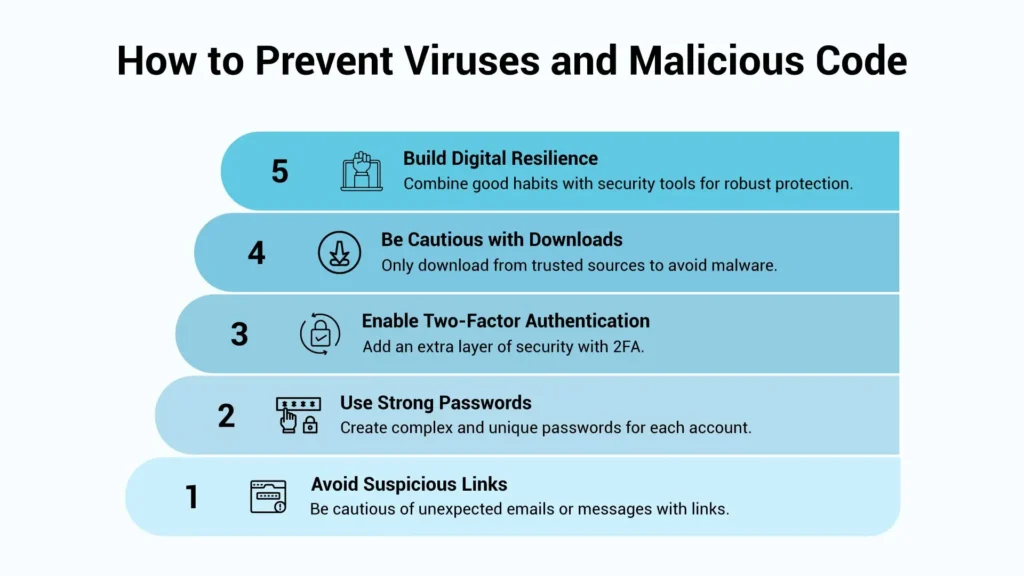
How to Prevent Viruses and Malicious Code: Practice Smart Digital Habits
Even the best antivirus software can only do so much if your online habits aren’t up to par. Truth is, human behavior is often the weakest link in digital security. So, if you’re wondering how to prevent viruses and malicious code, the answer isn’t just in the tools, it’s also in your day-to-day decisions.
Step 1: Avoid Suspicious Links
Let’s start with something simple: avoid suspicious links. If you get an unexpected email or a sketchy message with a link, even if it looks familiar, pause. Hover over the URL. Ask yourself if it makes sense. A moment of caution can prevent hours (or days) of cleanup.
Step 2: Use Strong Passwords
Next, use strong passwords. It sounds basic, but people still use “123456” or “password” far too often. Choose something complex, unique, and not repeated across accounts. Yes, it’s a pain to remember, but password managers can help with that.
Step 3: Enable Two-Factor Authentication (2FA)
Then there’s two-factor authentication (2FA). It’s not foolproof, but it adds a second hurdle for hackers. A one-time code sent to your phone or email might be the very thing that keeps someone from getting in.
Step 4: Be Cautious with Downloads
Also, be cautious with downloads. If you’re not 100% sure about the source, don’t download it. That “free” software or plug-in might come with a hidden cost.
Step 5: Practice Mindful Digital Habits
These habits don’t require tech skills. Just mindfulness. Think of them as your personal firewall, small, intentional actions that keep your system clean and your data secure.
Data Backup is Your Safety Net — Use It the Right Way
No one likes thinking about worst-case scenarios, but when it comes to cybersecurity, a little paranoia goes a long way. Because let’s face it: even with strong defenses, things can still go wrong. That’s where a good backup strategy comes in. It’s your safety net. If you get hit by ransomware, suffer a hardware failure, or accidentally delete a critical file, having a backup means you’re not starting from zero.
Start with regular data backups. Don’t just set it and forget it. Whether it’s daily, weekly, or monthly, consistency is key. The more current your backup, the less you lose if something goes wrong.
Then there’s the physical route, use external drives. Keep them disconnected when not in use. This way, if your main system is infected, your backup stays untouched.
And of course, don’t overlook cloud storage. Platforms like Dropbox offer secure data storage solutions that are not only off-site but accessible from virtually anywhere. That flexibility can be a lifesaver in a pinch.
It’s simple: you back up because the alternative is much worse. With just a few smart steps, you can make sure your important files are recoverable, no matter what comes your way.
Enterprise-Grade Protection: What Every Business Must Implement
For businesses, digital security isn’t just a technical concern, it’s a core part of operational stability. One breach can mean lost data, disrupted operations, and damaged trust. That’s why virus protection for business needs to go far beyond basic antivirus software.
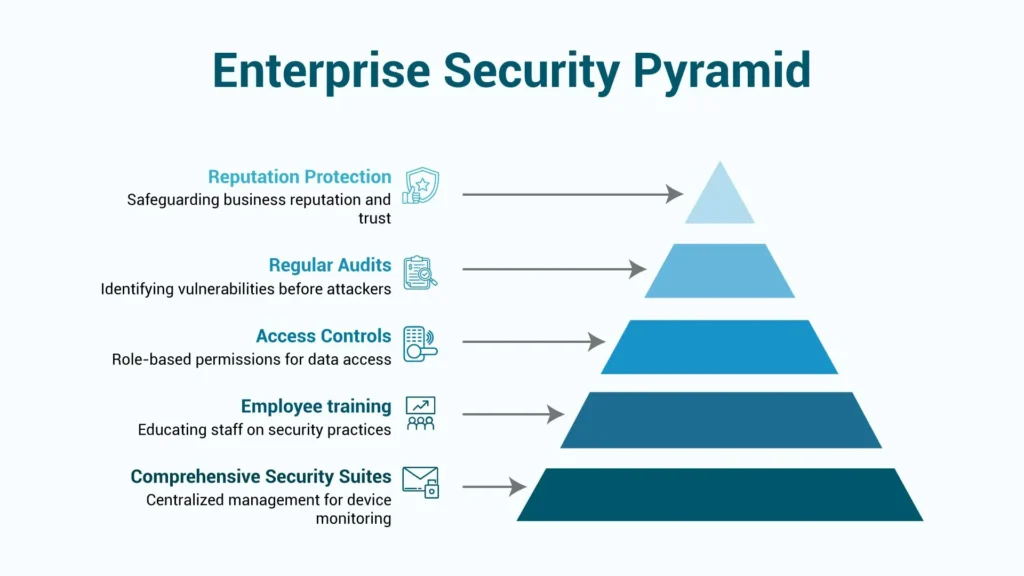
Start with comprehensive security suites like Bitdefender GravityZone. These tools offer centralized management, making it easier to monitor multiple devices, apply consistent policies, and respond quickly if something goes wrong. For businesses with remote teams or sensitive data, that kind of control is essential. As noted by sources like Security.org and WIRED, these enterprise-grade solutions aren’t optional anymore, they’re a baseline.
But software alone isn’t enough. Employee training is often the missing piece. A single careless click can undo even the best technical defenses. Routine training sessions, especially around phishing and password practices, can drastically reduce risk.
Access controls are another must. Not every employee needs access to every file. Implementing role-based permissions ensures that sensitive information stays in the right hands.
And finally, conduct regular audits. You can’t fix what you don’t see. Assessing your systems helps identify hidden vulnerabilities before attackers do.
Ultimately, protecting your business digitally is also about protecting your reputation. And that’s something no company can afford to overlook.
What to Do If You’re Already Infected
So, you think your system might be infected. Maybe it’s running unusually slow, programs are crashing, or strange pop-ups keep appearing. If any of this feels familiar, don’t wait. When it comes to a potential virus infection, time is not your friend.
Disconnect from the Internet
First, disconnect from the internet. Seriously, just pull the plug or turn off Wi-Fi. This simple step can help contain the threat, stopping it from spreading to other devices on your network. It’s basic triage, but it can make a huge difference.
Run a Full Antivirus Scan
Next, run a full antivirus scan using your trusted security software. Whether you’re relying on tools from brands like CrowdStrike Holdings, Inc, Checkmarx, or even something recommended by Tom’s Guide, this is where detection and removal begins. Don’t rush it, let the software do a thorough sweep.
Restore from a Clean Backup
If the damage looks deep or if files are locked, restore from a clean backup. This is when your earlier prep work pays off, if you’ve been backing up regularly, recovery can be surprisingly smooth.
Seek Professional Help
Still stuck? Don’t try to muscle through it. Seek professional help. Experts from firms like CyberArk or others can diagnose and repair the issue properly.
Quick action minimizes damage. The longer you wait, the harder recovery becomes.
How to Prevent Future Attacks from Viruses and Malicious Code
Staying ahead of cyber threats isn’t a one-time fix, it’s an ongoing effort. To truly protect your systems, you need to think long-term. That means being proactive, not just reactive. So, if you’re serious about how to prevent future attacks from viruses and malicious code, it starts with adopting habits that evolve with the threat landscape.

Stay Informed
First, stay informed. Cyber threats change fast. New types of malware appear, old vulnerabilities resurface, and tactics shift constantly. A quick daily skim of security news or subscribing to threat alerts can make a big difference.
Regularly Update Security Protocols
Next, regularly update your security protocols. The strategies that worked a year ago might not cut it today. Evaluate your defenses regularly and adjust as needed, think of it as spring cleaning for your cybersecurity.
Invest in Advanced Security Tools
It also helps to invest in advanced security tools. Look for solutions that offer real-time monitoring, automated responses, and behavior-based threat detection. The smarter the tool, the faster it can stop something in its tracks.
Continuous Training
And finally, never underestimate the power of continuous training. Cybersecurity isn’t just an IT issue, it’s a people issue. Educating your team or family members on safe practices can stop problems before they start.
Vigilance is your best shield against future virus attacks.
Final Thoughts
In the ever-shifting world of digital threats, there’s no such thing as perfect protection, only smarter protection. So when asking, how can you prevent viruses and malicious code, the real answer lies in how prepared you are to adapt, react, and stay one step ahead.
It’s not just about having the right tools. It’s about using them wisely, staying informed, and developing habits that make you a harder target. Threats will continue to evolve, that’s a given. But with a layered defense and a bit of vigilance, you don’t have to live in fear of every click or download.
This isn’t just a tech issue. It’s a life issue. Your photos, your files, your privacy, your work, it’s all digital now. And that makes digital security personal.
So, take it seriously. Build your defenses, update them often, and don’t underestimate the power of small, consistent actions. Because in a world where the next attack is always a possibility, the strongest strategy is to be ready for it before it happens.
Stay alert. Stay sharp. And above all, take control of your digital life, because no one else will do it for you.
Author

Jay S. Allen, MCP, MCSA, MCSE, MCSE+ Security, is an experienced IT professional with more than 20 years in the industry. He specializes in delivering enterprise-level cybersecurity and IT support solutions tailored to small and mid-sized businesses. Through Techno Advantage, Jay is dedicated to helping organizations strengthen their security posture and achieve greater efficiency through smart, scalable technology solutions.