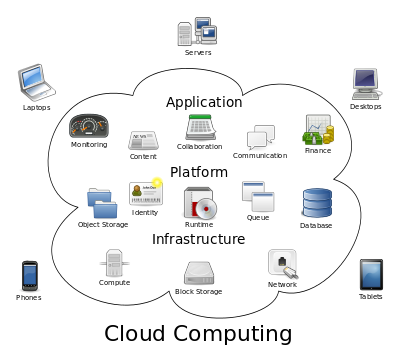
In today's digital age, safeguarding your business data is more critical than ever. Losing all your vital information in a flash—a fire, flood, or cyber-attack can wreak havoc and even force your business to shut down. That's why having a reliable Data Center Disaster...