Techno Blog
VoIP vs. Landline: Which is the Best Choice for Your Business?
In today’s hyper-connected world, communication is the lifeblood of any business. Whether you’re sealing deals with international clients or handling internal calls between teams, having a reliable phone system can make or break your operations. But when it comes to...
What is a Network Security Key and How Do You Find It?
In today's digital age, where practically everything from our personal information to our financial data is stored online, securing our wireless networks has never been more important. Whether you're working remotely, streaming movies, or just browsing the web, your...
What is Multi-Factor Authentication (MFA)?
Setting up a new laptop recently, as I reinstalled all my software and logged into my various tools, my phone was going nuts sending me codes. These codes are the Multi-Factor Authentication in action! Real-Life Security Issues During this same time, a client suddenly...
Top 4 Cloud-Based Storage Solutions with Must-Know Tips
When I started in IT, we stored our files on shared network drives, which existed in the same building and network. If you needed to reach a network drive outside that network, you had to have access to remote into that different network. Those documents were stored...
What is Remote Access Software?
Have you ever arrived at the office for the day, anxious about that big presentation you created and practiced last night, only to discover that you can’t find the flash drive containing the file ANYWHERE? With Remote Access Software, you can avoid the stress and...
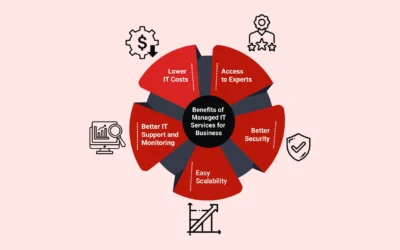
Top 13 Benefits of Managed IT Services for Your Business
The benefits of managed IT services are crucial in today's technology-driven world. So, businesses need to keep up with ever-evolving IT demands while ensuring that their operations run smoothly and securely. However, managing IT systems in-house can be a daunting and...
What is Granular Recovery Technology? A Comprehensive Guide
In today’s data-driven world, information is the lifeblood of organizations. From small businesses to large enterprises, data is the foundation of operations, decision-making, and strategy. With the increasing reliance on digital systems, the need to protect and...
Top 4 Data Backup Devices for Small Business
You already know you need good, regular backups of all of your business data, but you may get stuck figuring out the best way to manage them. Fortunately, you don't need to spend a scary amount of money to buy and set up a reliable backup system. Let’s look at a...
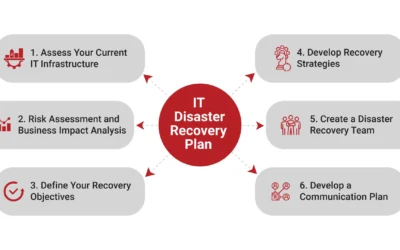
IT Disaster Recovery Plan: A Simple Guide
Imagine this: your business is running smoothly, customers are happy, and everything seems to be on track. Then, out of nowhere, a disaster strikes—maybe it's a cyberattack, a natural disaster, or even a simple hardware failure. Suddenly, your IT systems are down, and...
What is Data Backup and Recovery? A Comprehensive Guide
What is data backup and recovery? In today's digital age, data is the lifeblood of our personal and professional lives, and data recovery plays a crucial role in restoring lost or inaccessible information. From treasured family...
4 Rules of Business Email Etiquette Can Save Your Reputation
You may not think of email as having such power, but just as great email etiquette can bring in business, poor business email etiquette can drive customers away and ruin your reputation. And pretty quickly too, if these mistakes are repeated consistently. What...
What is a VoIP Caller? A Complete Guide
In the digital age, communication has drastically evolved, with one significant advancement being VoIP or Voice over Internet Protocol. If you've ever wondered, "What is a VoIP caller?" This guide is here to answer that. VoIP technology allows users to make voice...
How to Send a Secure Email: A Comprehensive Guide
Do you know how to send a secure email? Think of it like sending a letter—you want only the intended recipient to read it, right? Here's how to ensure your emails are just as private. For the most part, our important mail is sent in a sealed envelope to protect...
Is a VoIP Phone System Right For Your Business?
If you've never heard of VoIP and VOIP phone systems, get ready to change the way you think about long-distance phone calls. VoIP, or Voice over Internet Protocol, is a method for taking analog audio signals, like the kind you hear when you talk on the phone and...
The Importance of Data Center Disaster Recovery Plan
In today's digital age, safeguarding your business data is more critical than ever. Losing all your vital information in a flash—a fire, flood, or cyber-attack can wreak havoc and even force your business to shut down. That's why having a reliable Data Center Disaster...
Top 11 Mobile Marketing Strategies to Grow Your Business
In today's digital age, mobile marketing strategies are essential for any business looking to thrive. With the increasing number of people using smartphones, reaching customers through their mobile devices has never been more crucial. If you want to grow your business...
Top 10 Key Benefits of Software Management System
In today's tech-savvy world, work software systems are like the captain of a ship, steering businesses and organizations through the vast sea of digital tools and technologies. It's all about making sure that everything related to software, from creating it to using...
10 Key Steps on How to Secure a Network
Understanding how to secure a network is essential for protecting sensitive information and preventing unauthorized access. In fact, securing a network is super important in today's world where so much of our stuff happens online, like sending emails or doing banking....
The Most Common Types of Network Vulnerability Issues
Let's talk about something really important: network vulnerability. It's like having a secret door in your house that someone can sneak through if you don't lock it properly. Businesses and regular folks like us need to pay attention to this because our whole digital...
What is Data Mining?
Is your internet service provider doing data mining? Is that even legal? I don’t know about you, but I wish to keep my private life private. If this sounds like something we have in common, you might be asking yourself what your internet service provider is doing to...