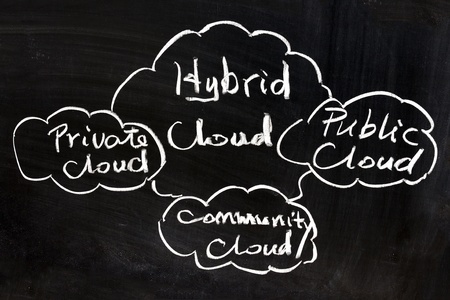
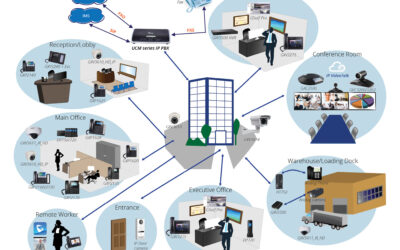
We are a year into this pandemic, and the office landscape has been forever changed. Both companies and employees learned what working from home looks like. It is not all good, or all bad. There is a lot of self-discipline that needs to take place and many employees...