Techno Blog
What Is a Softphone? Definition, Benefits, & How To Get One
When the pandemic started, we thought it was temporary, so employees were using their personal cell phones to keep in touch with clients and co-workers. But as it became more long-term, many companies realized they needed the features of the company phone system....
Business Laptop vs Consumer Laptop: Which One is Better?
In the realm of choosing a laptop between a business laptop and a Consumer Laptop can raise a question: Business Laptop vs Consumer Laptop – which reigns supreme? So, it's crucial to grasp the differences between the two. While consumer laptops may initially attract...
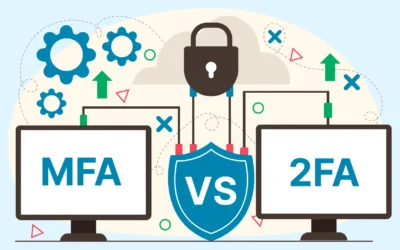
MFA Vs 2FA: What are the Key Differences?
We live in a world where keeping our online accounts safe is super important. Have you ever heard of terms like MFA or 2FA while setting up your account security? They may sound like tech jargon, but they're pretty important. So, MFA Vs 2FA, which would win the...
What Is Data Recovery Objective?
What is Data Recovery? Simply put, it's important to know what data recovery is because it sets out the reasons and aims for recovering data that has been lost or damaged. In today's digital age, where information is incredibly valuable, losing important data can have...
Your Service Provider and Your Data
Is your internet service provider mining your data? Is that even legal? Does Your Service Provider Protect Your Data? I don’t know about you, but I wish to keep my private life private. If this sounds like something we have in common, you might be...
Multi and Two-Factor Authentication Explained
The days of trusting passwords (single factor authentication) alone are ending, my friends. What Are MFA And 2FA? Perhaps you have been asked to add MFA or 2FA to your online banking account or Amazon. MFA and 2FA...
Could a Password Manager Halt Hackers?
According to the FBI, 58% of Americans have experienced a data breach of some kind. Of those, 21% reported compromised Financial Accounts (banking, credit, PayPal, Venmo), 19% had their Email Accounts hacked, and 18% experienced a breach in the security of their...
Creepers vs Reapers: The Original Virus and Anti-Virus Duo
Did you know that the first computer virus was called The Creeper? In the early 70’s, two computer scientists named Bob Thomas and Ray Tomlinson created two Creeper viruses - one that couldn’t self replicate and one that could. In order to remove these viruses from...
The Network Security Process: Firewalls Explained
In the tech industry, the scary stories we tell around the campfire sound just a little different than your typical urban legends. Our tales of fright don’t need ghosts or goblins…we’ve got predatory Hackers and insidious Malware to spook us! Just recently a bank here...
Data Disaster Recovery Plan
You can ask anyone who has ever experienced the horror of data loss, and they will all tell you the same thing; They didn’t think it could happen to them. The question is not “Will I ever experience data loss?” but rather, “By what means will I experience loss? When,...
*Beep* *Beep* *Beep* Let’s Talk Backup Plans
Are you curious about what to do in case of a hard drive crash, malicious malware attack, or accidental file deletion? Have you ever wondered if you should backup your files, but aren’t sure which option is best for you? In this month’s blog, we will be addressing...
My Data Was Kidnapped!
Business owners face so many challenges and worries: staffing problems, equipment failure, packages not getting delivered, financial troubles…just to name a few. But as a small business owner, I have never worried about Ransomware Attacks. Isn’t that what happening on...
“What do you mean ‘the system is down!’, it can’t be down! We have work to do!”
Social media was a buzz today, because Facebook, Instagram and WhatsApp were down. You might have been one of the people who didn’t miss it at all, or your business might rely on these platforms to reach their clients. International businesses use WhatsApp for calls....
Do you have the bandwidth you need?
In conversation the other day a parent said, “I just don’t have the bandwidth for this teen drama today.” My nerdy mind immediately thought about 1’s and 0’s passing through space. Bandwidth is now a buzz word, according to the Urban Dictionary, for how well someone...
DYI – How To Back Up & Keep My Phone Photos!
I love when our readers will send us in questions! Last week, we got this question…” I take a lot of photos with my phone, but now I’m running out of space. How can I best back them up and keep the accessible for years to come?” -Suzy T. I hear ya, Suzy! I take a lot...
Working on updates…Don’t turn off your PC
It never fails. If I’m running late for an early meeting, I open my laptop and there it is. The blue screen telling me, “Working on updates… 20% …Don’t turn off your PC.” This seems to always come up at the most inconvenient time. If given a choice, I will normally...
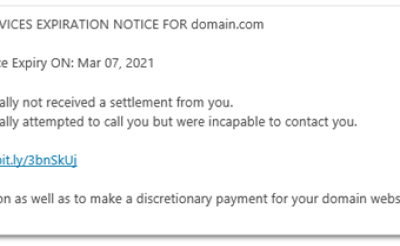
Protect your Domain – No Phishing Allowed!
Do you know when your domain expires? Most companies don’t track those things; they wait for the invoice from their Domain service or website hosting provider. So, when they receive an email like this one, they go ahead to renew it. After all, no one wants to lose...
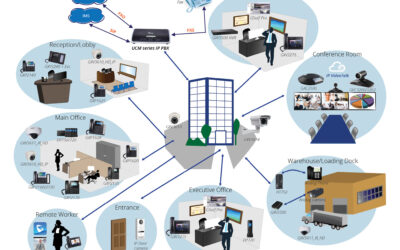
Grandstream Phone Solution
We are a year into this pandemic, and the office landscape has been forever changed. Both companies and employees learned what working from home looks like. It is not all good, or all bad. There is a lot of self-discipline that needs to take place and many employees...
New Year’s Resolution “Use Phones More Effectively”
In our last blog we talked about how to use email more effectively. We got some great reactions and comments about it. As mentioned, it was a part 1 of the New Year’s Resolutions, we are hearing often. So, what’s the second resolution business owners are making? “I...
New Year’s Resolution “Use Email More Effectively”
The calendar now says 2021, and already it has been an interesting year, unlike any other. Like each year, we hear about creating “New Year’s Resolutions”, but this year, we are hearing about resolutions involving technology. One of the resolutions brought to our...